
06 Jan Gartner’s 2020 Predictions – Adaptive Security
In 2019, Gartner announced their top 10 identified government technology trends for 2019/2020. Predictions are hard, especially when they’re about the future, and it’s pretty likely that Gartner hadn’t factored in an impending worldwide pandemic when they wrote these, but let’s kick off a new year and revisit them for completeness, rate them in terms of relevance, and see how Dinode’s xMS platform incorporates each of these elements.
Trend #1 – Adaptive Security
Gartner Says:
“An adaptive security approach treats risk, trust and security as a continuous and adaptive process that anticipates and mitigates constantly evolving cyber threats. It acknowledges there is no perfect protection and security needs to be adaptive, everywhere, all the time.”
Security is such an enormous and heavily laden term, especially when applied to government. When thinking about security in a technology sense, I find that it helps to break security down into three separate component parts:
People Security
People Security deals with individuals and their behaviour. In this category, I put solutions like SIEM and Intrusion Detection, User Behaviour Analytics, Permissions, Access Control, Caveats and other rights granted or denied to people.
Application Security
Application Security deals with how hackable our software and hardware technology solutions are. Can they be easily compromised? Can they be fooled into elevating privileges or executing foreign code?
Data Security
Data Security is the last line of defence, and deals with information itself, protecting access and encrypting it so that it can only be of use to people who have permission to see and use it.
Looking at these components, it’s easy to see that what is true at one point in time, may not be true at another. Encryption can be broken, systems for monitoring can themselves be prone to security violations or down time, new zero-day exploits in software dependencies are constantly being discovered. In short, the solutions that we put in place to protect our systems today, may not provide us absolute protection tomorrow. Our enterprise software isn’t a fortress – it requires constant improvement, patrolling and active monitoring to ensure that it’s secure.
The approach that we’ve seen from enterprise and government customers is that security is generally paramount when purchasing and evaluating a solution – but then becomes easier to overlook when dealing with deployment issues , and often isn’t regularly reviewed as people and systems change.
COVID-19 has, if anything, highlighted how important it is to take an adaptive approach to security. This recent report from accenture highlights the unique challenges for security brought about by the pandemic, most notably:
“…Organizations are rethinking their culture, collaborative practices, and the technology necessary to enable distributed working environments at scale…”
Again – it’s significant change that adds risk – often at the cultural and people level of security.
From our side, while building Dinode xMS, security has been central to everything we’ve built. As a general rule, we wanted to avoid storing any passwords or doing any security authentication in our platform. Most enterprise customers already have an established authentication framework, and a requirement for Single Sign On (SSO) – so xMS supports all modern authentication frameworks. In addition to that, we support multiple frameworks. So, if two government departments wanted to collaborate on an xMS Application, they could each use their own existing authentication systems.
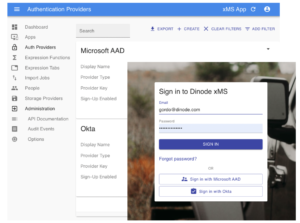
xMS lets you define the authentication providers you use, and fits in with your existing security authorisation solution, as well as using multiples to share apps across identity domains.
Of course, knowing who you are is only part of the equation – the next problem is determining what you can do.
In our experience, enterprise systems require very granular levels of access security. Users of a system may be able to see some properties of an object, but not all of them. They may be able to edit certain fields, but not others based on their role. So in xMS, we added a fine grained security permissions infrastructure that respects that. The role that a user is assigned determines what level of visibility they have over xMS Entities, and the fields that are on them, and application designers can decide, down to the field level, what people can see, edit, update and delete.
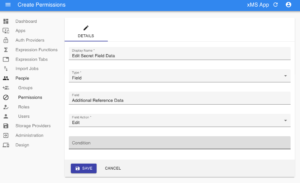
xMS offers extra fine grained security – for groups, roles, users, entity types and fields – ensuring that you can adapt your security to meet requirements
Users can also be in multiple roles. This allows for an application designer to design profiles that match the ideal security profile. And of course, in keeping with adaptive security practices, these can be changed and updated at any time, without changing the configuration of the system or the underlying data.
From an application security side, the xMS platform itself will be regularly tested and evaluated against possible security breaches and known exploits. Our certificates from our test agency will be available to customers for review on request. Again, with an adaptive focus, we are constantly patching and updating the platform to stay one step ahead of the bad guys – and this is one less thing that customers building apps on the xMS platform have to worry about – leave that to us.
And as for Data Security, we use AWS for all our storage – (but we will in future support other cloud providers.) AWS does some great stuff to ensure that data stored in the platform is secure – AWS environments are continuously audited, with certifications from accreditation bodies across geographies and verticals. Every instance includes DDOS Mitigation and built in redundancy using auto scaling and elastic load balancing. We also encrypt all data at rest and in flight, to ensure that your information is only available to those who need to be able to see it.
In addition to all these, we have a relentless commitment to transparency, so everything that ever happens in any xMS app is captured in detail in the audit events log.
In conclusion, Adaptive Security seems like a pragmatic and sensible approach to security in general, and while we’re not sure that most government agencies are there yet, it’s definitely forming a key part of security planning in government agencies. It’s been a big part of our thinking too, while building xMS in the last 18 months.
Our Rating: Relevant. This Trend was important all through 2019 and 2020, and seems likely to remain more so going forward.
If you’d like to chat with us about how you can use xMS to build your next solution and fit in with your security strategy, please get in touch!




Sorry, the comment form is closed at this time.